The economics of privacy
Information is power and is readily monetized.
It is one thing to design a technology that provides full functionality while preserving consumer privacy, but it is another thing to have the private technology adopted in industry. On one side, the consumer wants his or her individual privacy. On the other, the service provider and large corporations want as much consumer information as they can get their hands on. We can use game theoretic frameworks to weigh up the benefits and costs to the consumer of various policy options and determine the economic conditions required to push the industry towards opting for private technologies as the Nash equilibrium strategy tuple.
Accurately determining the benefits and costs to all players of various regulatory policies can help in deciding which is the most effective for implementation.
How can we design regulatory or governmental policies that will allow for the adoption of private technology? The key is to determine a valuation for the privacy of an individual. However, this is an extremely difficult problem, because individuals value their privacy in very different ways. Some individuals may have no desire for personal privacy, while others may be extremely sensitive. Both are acceptable. Furthermore, various demographic factors can bias subsets of the population in different ways.
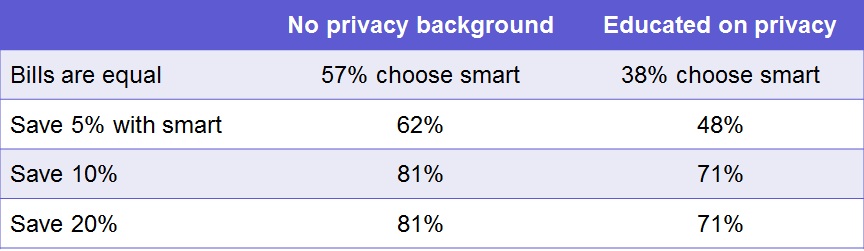
The simplest way to determine a valuation of privacy for the individual is to use modern survey methodologies. In this light, we have conducted national surveys to determine individual consumers' valuation of their privacy (or information) in the contexts of smart metering and cellular technology. Initial pilot results show interesting results, indicating that in general, consumers are very sensitive to their privacy in these contexts.
Survey research and logistic regression can help determine the value of privacy.
We are currently running this survey research and plan to employ logistic regression methods to determine a definitive value for individual privacy.
A privacy-aware smart metering infrastructure
It's been established that smart meters can harm consumer privacy. The issue is that smart meters are being designed to enable demand response (DR). DR can reduce the production costs of electricity and allow consumers to take advantage of real-time electricity prices, thereby reducing consumer bills. However, to enable this, the utility companies will need to collect temporally precise power consumption data at the individual household level. This compromises consumer privacy, as the figure below shows.
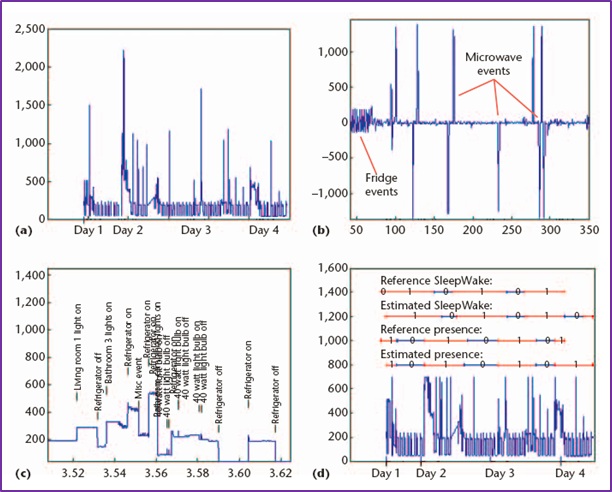
Identifiable consumer behavior [4]: (a) aggregate power consumption data; (b) derived switch events; (c) load events; (d) reference and estimated presence intervals. [Lisovich et. al.]
The figure above shows the temporally precise electricity consumption at a household. From the graphs, we can see exactly when individuals in the household are doing particular things - such as opening the fridge, throwing a party, taking a shower, or leaving home. That's very sensitive information that should not be in the hands of a third party.
To address this issue, we need to design the smart grid and smart metering infrastructures from a privacy-aware frame of mind. We suggest the use of a set of privacy-aware principles for engineering design, which uses policies prescribed by the US DHEW (now the US DHHS) and sets forth a modern framework for technology design. Following this framework, we can develop a privacy-aware network for smart metering using a combination of encrypted communication and aggregation of information for increased anonymization of data.
Designing a privacy-aware vehicle-to-grid network
Vehicle-to-grid (V2G) proposes integration of battery-powered electric drive vehicles into the grid, enabling them to be recharged as well as act as suppliers in the ancillary service markets. That's expected to create incentives for the production and adoption of electric vehicles in the automotive industry. V2G requires that the utility company or a third party has access to each vehicle's charging status via a two-way communication network for billing and planning purposes.
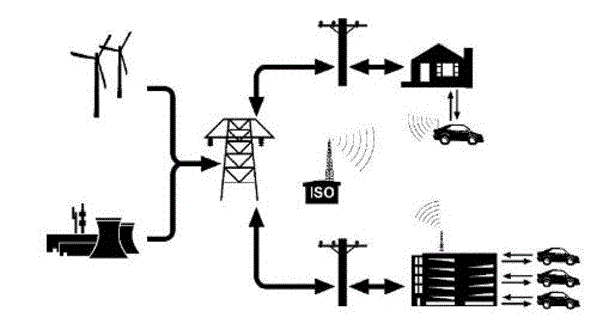
The V2G concept. [connectedvehicle.challenge.gov]
However, there are consumer privacy risks associated with V2G implementation; consumer preferences and behaviors can be inferred from charging information if privacy is not a primary concern from the outset of V2G design.
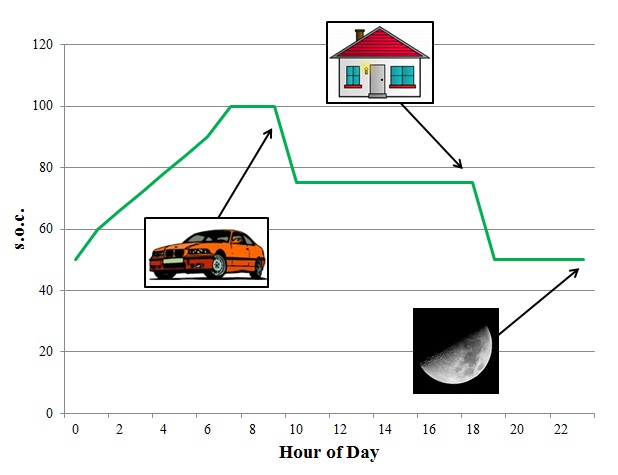
A typical electric vehicle battery's charging profile measuring battery charge % throughout the day.
The charging profile for a typical PHEV user is shown in the figure above. Note that we can tell when the individual leaves and returns home. We can also infer how far away the individual's workplace is from his/her home. Finally, we know that s/he owns a PHEV. However, even more information can be revealed if we assume that the consumer's identity (in the form of a battery ID number that is associated with a household and billing method) and location of charging are also items of interest to the aggregator for data collection. It can be expected that utility- or aggregator-owned charging stations will be available for consumers to use at parking spaces at the workplace, mall, grocery, parking meter, and other commercial locations. To enable billing, the charging station will need to communicate the battery's ID number to the utility company or the aggregator, revealing the address-precise location of the PHEV. Given charging location, your utility company would be able to infer sensitive information including the location of your residence and workplace, the identities of your friends, your doctor's identity and your history of hospital visits, your shopping preferences and the locations of businesses you frequent, and more.
Given this, how can we protect consumer privacy while still allowing for full V2G and PHEV functionality? We would need to approach the design of V2G from a privacy-aware perspective, respecting the fact that privacy needs to be an engineering goal. Using a series of encryped communication protocols in conjunction with the use of a Trusted Platform Module, we can approach a privacy-aware vehicle-to-grid framework with the following design.
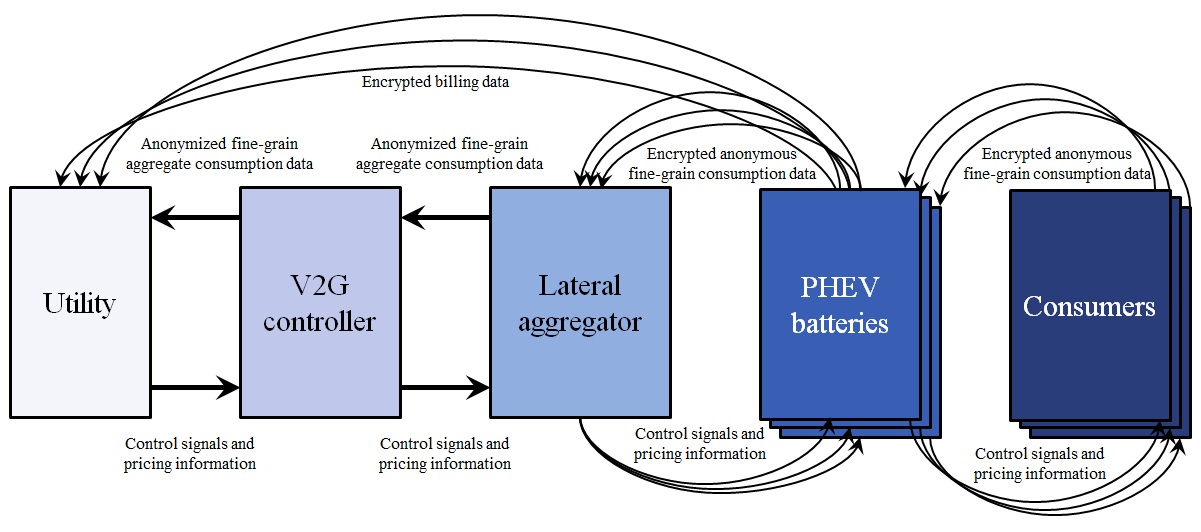
Privacy-aware V2G framework.
This design takes advantage of the nature of the power system. Aggregated information at the distribution network level is all the utility company requires for efficient planning capability. That is, they do not require data at the level of the individual consumer. Therefore, we can use aggregation and encryption while still enabling all required functionality of the V2G system, including the economic and infrastructural structures around the charging, planning, and billing mechanisms.
Electricity market auction mechanisms
The Independent System Operators (ISOs) that oversee wholesale electricity markets in the U.S. use an auction mechanism to select supply and demand bids in the day-ahead market for energy and ancillary services. Subsequently, a pricing algorithm is executed to determine Market Clearing Prices (MCPs) or congestion-dependent Locational Marginal Prices (LMPs). Presently, ISOs employ the "bid cost minimization" (BCM) auction method that minimizes the total bid cost given the set of bids. However, since generating companies may not bid according to their true production costs, bid cost minimization may not always equate to social welfare maximization.
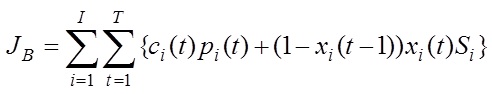
Bid cost minimization objective function
It has been shown recently that an alternative method of auction selection, known as "payment cost minimization" (PCM), results a in lower cost of energy for consumers than BCM does for a given set of supply bids for a day, where demand is assumed given for simplicity.
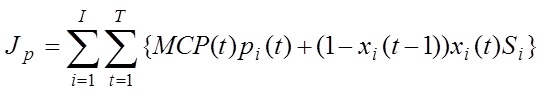
Payment cost minimization objective function
However, while the use of PCM minimizes consumer payments for a given set of bids for a day, it had not been fully illustrated that PCM minimizes payments over a longer time period with intelligent bidders that can adjust to the new auction mechanism. To address this, I developed a novel discrete game theoretic method of bidder behavior to model the competitive nature of generating companies in the day-ahead market. My numerical testing results show that PCM significantly reduces consumer payments with intelligent bidders.
![]()
Nash equilibrum solution methodology
Additional testing with a market simulator was used to support my initial results.

Economic comparison of BCM and PCM
In this work, we confirmed the potential advantages of PCM and showed that the new auction mechanism can provide up to 12% lower payment costs for consumers in the long term.
Publications
J. Tse, D. Schrader, D. Ghosh, T. Liao, and D. Lundie, “A bibliometric analysis of privacy and ethics in IEEE Security and Privacy,” Ethics and Information Technology, 2015.
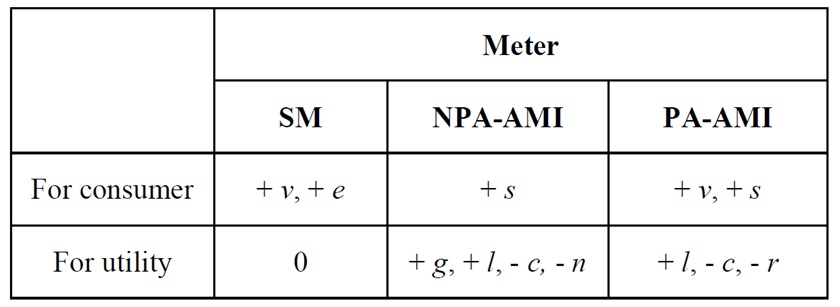
D. Ghosh, D. Schrader, S. Wicker, J. Yan, T. Leong, and W. Schulze, “Quantifying the effect of media on privacy: How advertising affects consumer willingness to pay for privacy in smart metering,” Media in Transition 8, MIT, Cambridge, MA, 2013.
D. Schrader, D. Ghosh, W. Schulze, and S. Wicker, “Civilization and its privacy discontents: the personal and public price of privacy,” Privacy Law Scholars Conference, Berkeley, CA, 2013.
D. Ghosh, R. Thomas, and S. Wicker, “A Privacy‐Aware Design for the Vehicle‐to‐Grid Framework,” 46th Hawaiian International Conference on System Sciences (HICSS‐46), Maui, HI, 2013.
D. Ghosh, D. Schrader, W. Schulze, and S. Wicker, “Economic Analysis of Privacy‐ Aware Advanced Metering Infrastructure Adoption,” IEEE Innovative Smart Grid Technologies (ISGT), Washington, DC, 2012.
D. Ghosh, S. Wicker, and L. Blume, “Game Theoretic Analysis of Privacy‐Aware Advanced Metering Infrastructure,” IEEE Innovative Smart Grid Technologies (ISGT), Manchester, UK, 2011.
D. Ghosh and P. Luh, “Analysis and simulation of payment cost minimization and bid cost minimization with strategic bidders,” IEEE Power Systems Conference and Exposition (PSCE), Phoenix, AZ, 2011.